Authentication with SmartBear ID
This article applies to accounts that use SmartBear ID for authentication. This includes all accounts created on or after Dec 11th 2023. For customers on Cognito see this guide.
To determine which authentication mode is enabled on your account, consult the following table:
| SmartBear ID | Cognito | Both |
|---|---|---|
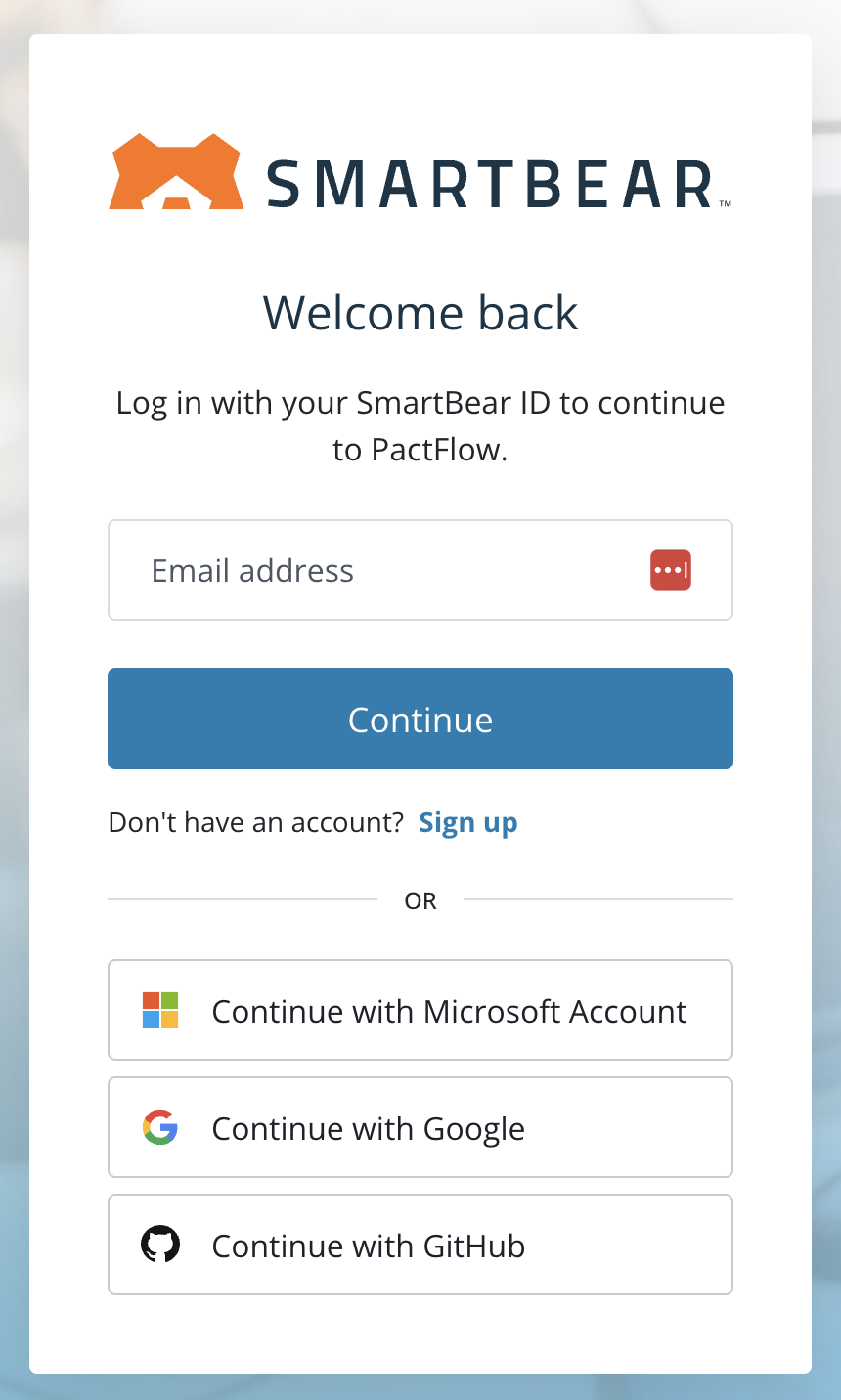 | 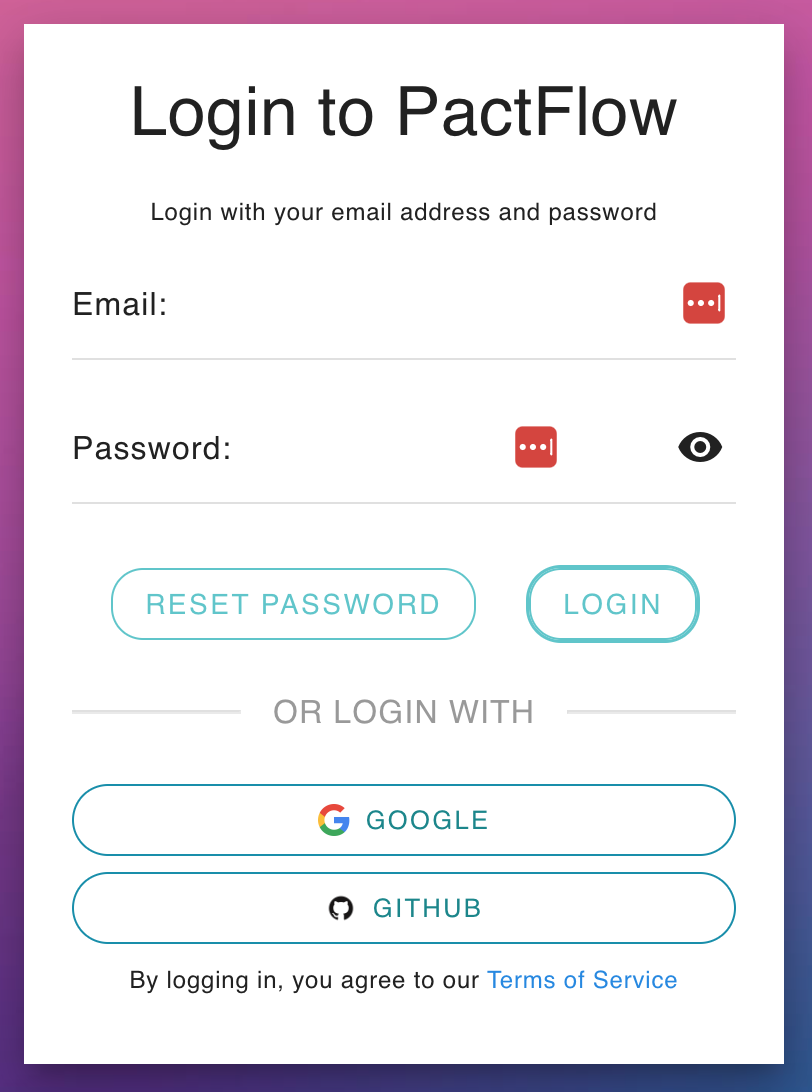 | 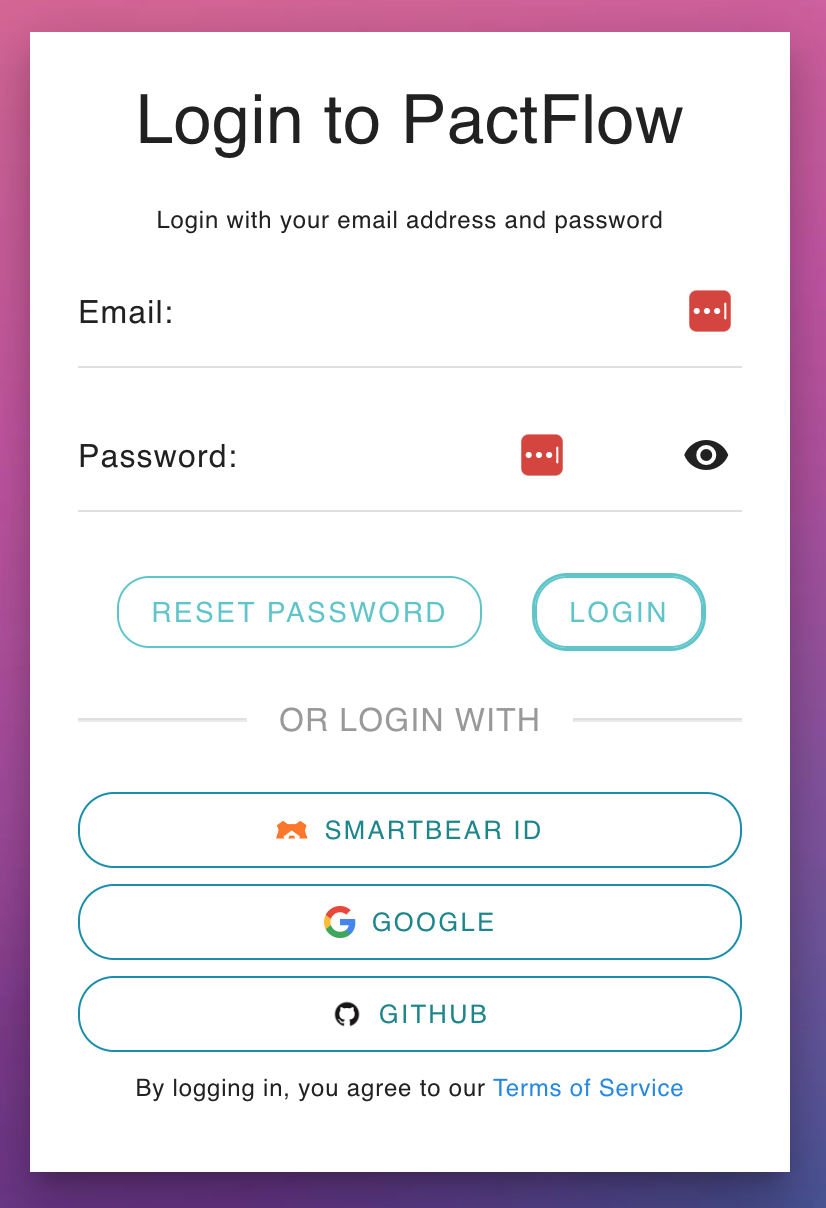 |
| If you only see this page when you visit your PactFlow Account, you are fully transitioned to SmartBear ID. | If you see a login page like this, you are on our Cognito authentication. See this guide. | If there is a "SMARTBEAR ID" button on your login screen like this, you have both enabled and are in the process of migrating to SmartBear ID. |
Account Invitation and Registration
PactFlow users authenticate with SmartBear ID. See the SmartBear ID Documentation to learn about the login process and options.
Regardless of how a user authenticates, all users must first be invited by a PactFlow administrator before access is granted. See the guide on User Administration. Once a user has been invited, they will receive an invitation email requesting they login or create an account.
Social Logins
Eligible plans: all
SmartBear ID supports social login access via Github, Google, and Microsoft. During account registration, the user can choose their preferred login option.
SSO with SAML 2.0
Eligible plans: Enterprise
PactFlow supports SAML 2.0 integration with a compatible Identity Provider (IdP) such as Okta, Ping, Auth0, Azure AD, OneLogin etc.
SAML2.0 allows you to externalise the authentication and access to your PactFlow account. Authorization and fine-grained permissions are managed within your account by an account Administrator.
We do not currently support the following:
- Automated user deprovisioning (users will appear "active" and count toward user limits, although will not be able to login if disabled in the IdP)
- IdP initiated login
- Service Provider (SP) initiated logout flow
- SCIM*
Once SAML 2.0 has been configured on a PactFlow instance, all users for the email domain are forced to authenticate via SAML 2.0, even if they had previously registered a username/password or social login.
Troubleshooting
1. I've enabled SSO, can I disable login via username/password?
Once SSO has been enabled, any users on the registered SAML domain must login using SAML - logging in via email/password or a social login is disabled.
Users not attached to the SAML domain that have been invited may login using any form. Inviting users is controlled by the user:invite permission, which by default is only available to Administrators.
We recommend at least one administrative user who can login with a username and password to address break-glass scenarios (for example, if your SSO provider is down or misconfigured).
2. I'm an enterprise customer and need SCIM enabled
Please contact your Account Manager so that we can enable our legacy authentication on your account.